All Of The Following Are Issues Of Computer Security Except
Providing correct data to unauthorized individuals b. Permitting computer operators unlimited access to the computer room c.
 All Of The Following Are Issues Of Computer Security Except A Releasing Course Hero
All Of The Following Are Issues Of Computer Security Except A Releasing Course Hero
all of the following are issues of computer security except
all of the following are issues of computer security except is a summary of the best information with HD images sourced from all the most popular websites in the world. You can access all contents by clicking the download button. If want a higher resolution you can find it on Google Images.
Note: Copyright of all images in all of the following are issues of computer security except content depends on the source site. We hope you do not use it for commercial purposes.
Permitting access to data by unauthorized d.
All of the following are issues of computer security except. Releasing incorrect data to authorized individuals b. Protection from viruses worms and other threats b. Permitting computer operators unlimited access to the computer room c.
Providing correct data to unauthorized individuals. Releasing incorrect data to authorized individuals c. All of the following are issues of computer security except b permitting computer operators c.
As a computer user who is dependent on technology to do your job you have certain rights and responsibilities. The ability to recover and read deleted or damaged files from a criminals computer is an example of a law enforcement specialty called. Analysis of the fire detection system at the primary site.
Providing correct data to unauthorized individuals. All of the following are issues of computer security except a. All of the following are issues of computer security except a.
Permitting access to data by unauthorized individuals d. All of the following are issues of computer security except a. All of the following tests of controls will provide evidence about the physical security of the computer center except.
All of the following are examples of real security and privacy risks except. Releasing incorrect data to authorized individuals b. Which of the following is true.
Permitting access to data by unauthorized individuals. All of the following tests of controls will provide evidence about the adequacy of the disaster recovery plan except. Permitting computer operators unlimited access to the computer room c.
Your rights include all of the following except having. Releasing incorrect data to authorized individuals b. All of the following are issues of computer security except a releasing from accounting 10013229 at university of ghana.
Computer hardware and programs that allow you to perform your job proficiently d. Verification of the second site backup location. Permitting access to data by unauthorized individuals d.
Providing correct data to unauthorized individuals. Permitting computer operators unlimited access to the computer room d. Permitting access to data by unauthorized individuals d.
A secure computing environment c. Providing correct data to unauthorized individuals. All of the following are issues of computer security except.
Https Onlinelibrary Wiley Com Doi Pdf 10 1002 9781119204206 Oth01
 What Are Cyber Threats And What To Do About Them The Missing Report
What Are Cyber Threats And What To Do About Them The Missing Report
 Soal Gslc Isa Docx Multiple Choice 1 All Of The Following Are Issues Of Computer Security Except A Releasing Incorrect Data To Authorized Individuals Course Hero
Soal Gslc Isa Docx Multiple Choice 1 All Of The Following Are Issues Of Computer Security Except A Releasing Incorrect Data To Authorized Individuals Course Hero
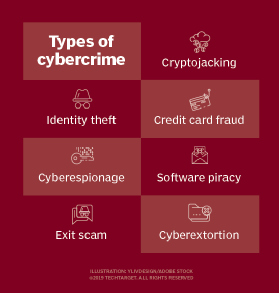 What Is Cybercrime Effects Examples And Prevention
What Is Cybercrime Effects Examples And Prevention
 What Are Cyber Threats And What To Do About Them The Missing Report
What Are Cyber Threats And What To Do About Them The Missing Report
Https Www Itu Int Dms Pub Itu D Opb Str D Str Gci 01 2018 Pdf E Pdf
 Cybersecurity 101 Protect Your Privacy From Hackers Spies And The Government Zdnet
Cybersecurity 101 Protect Your Privacy From Hackers Spies And The Government Zdnet
 What Is Malware And How Does It Work
What Is Malware And How Does It Work
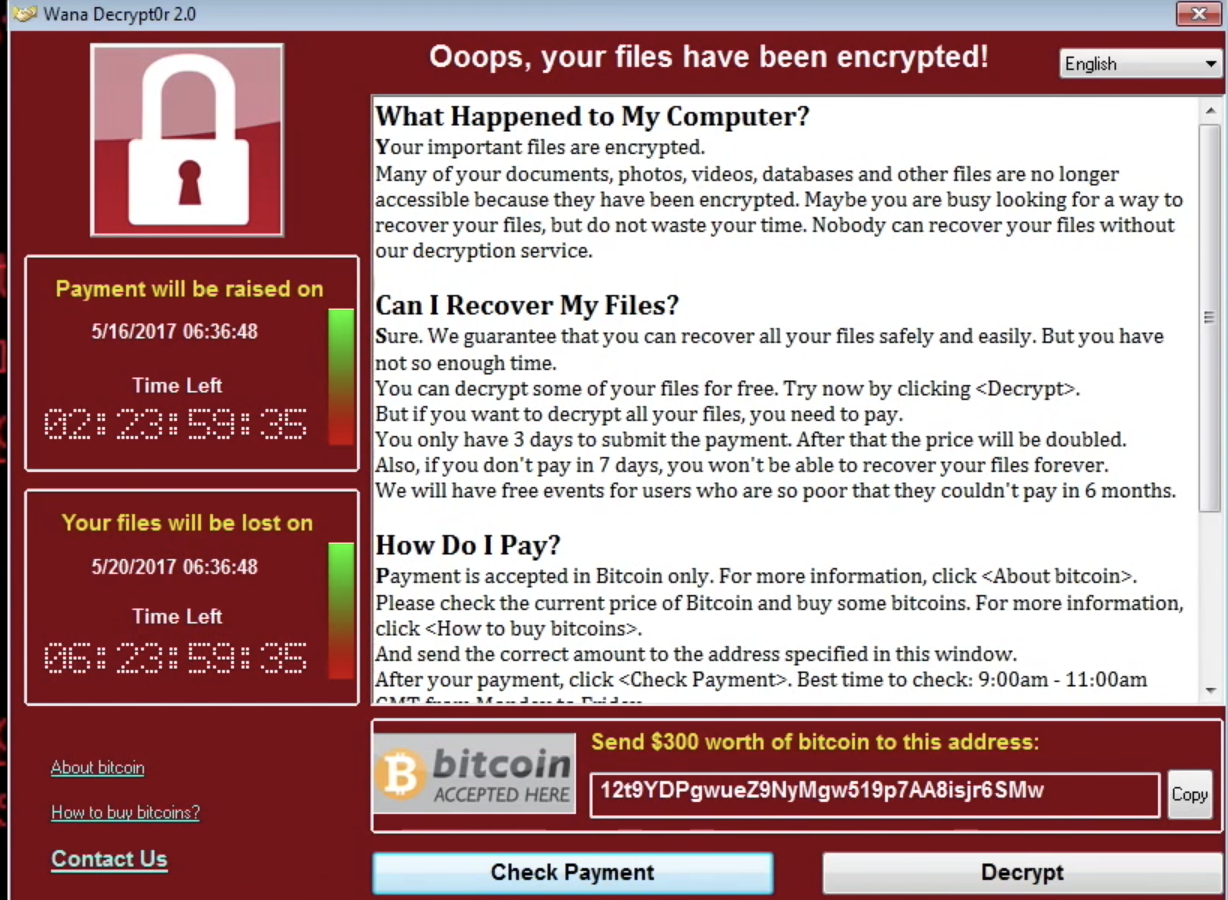 The History Of Cyber Security Everything You Ever Wanted To Know Sentinelone
The History Of Cyber Security Everything You Ever Wanted To Know Sentinelone
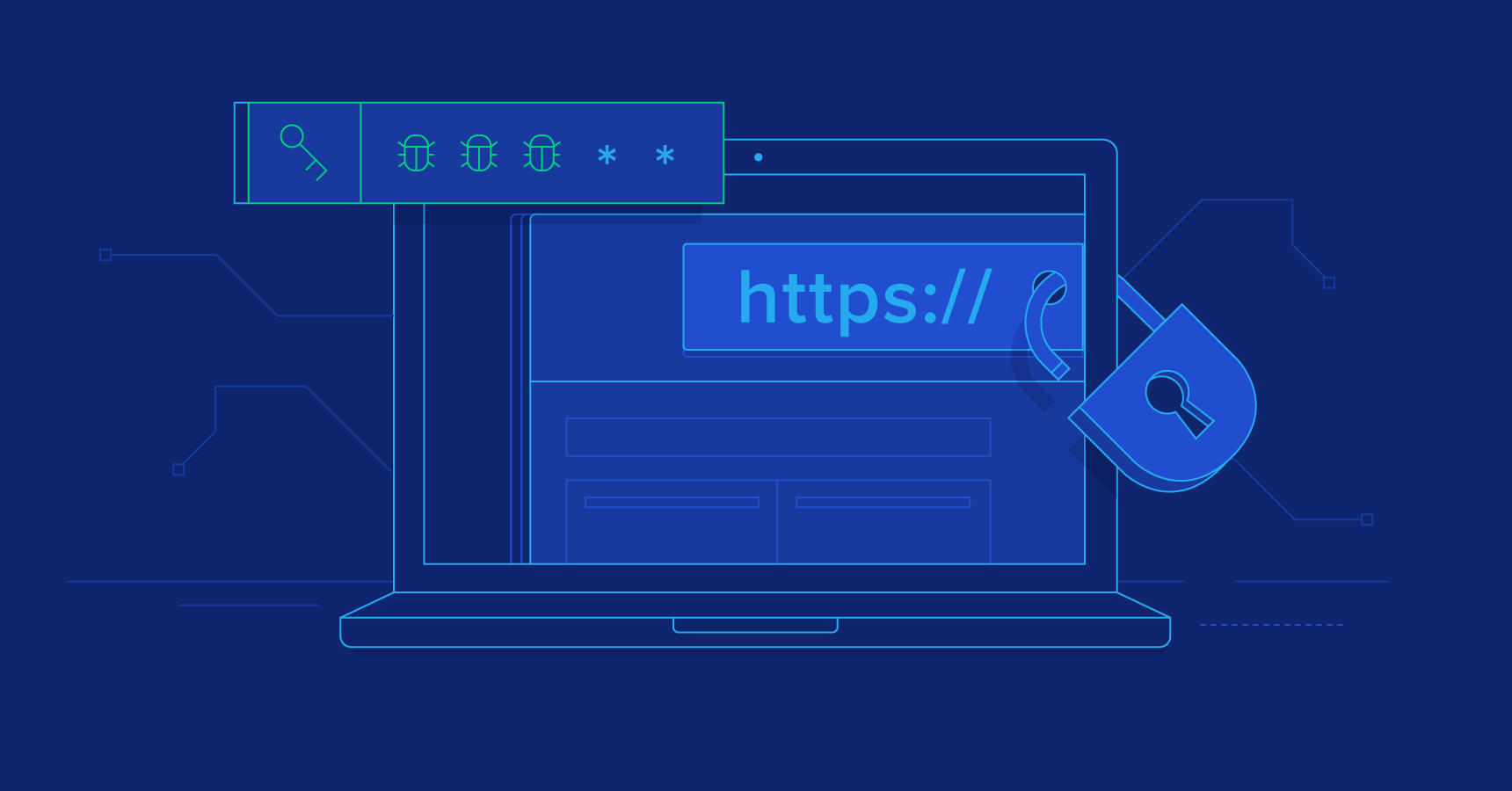 10 Web Security Vulnerabilities You Can Prevent Toptal
10 Web Security Vulnerabilities You Can Prevent Toptal
 Cybersecurity 101 Protect Your Privacy From Hackers Spies And The Government Zdnet
Cybersecurity 101 Protect Your Privacy From Hackers Spies And The Government Zdnet