A Hybrid Intrusion Detection System Design For Computer Network Security
With an viewers response system college students and learners are likely to take part actively in the class room periods. It detects the malicious traffic data on a.
 Pdf A Hybrid Intrusion Detection System Design For Computer Network Security Semantic Scholar
Pdf A Hybrid Intrusion Detection System Design For Computer Network Security Semantic Scholar
a hybrid intrusion detection system design for computer network security
a hybrid intrusion detection system design for computer network security is a summary of the best information with HD images sourced from all the most popular websites in the world. You can access all contents by clicking the download button. If want a higher resolution you can find it on Google Images.
Note: Copyright of all images in a hybrid intrusion detection system design for computer network security content depends on the source site. We hope you do not use it for commercial purposes.
Idss collect network traffic information from some point on the network or computer system and then use this information to secure the network.

A hybrid intrusion detection system design for computer network security. Intrusion detection systems can be misuse detection or anomaly detection based. Intrusion detection system ids essentially fits in as a unit which monitors the user activities incoming traffic and then distinguishes or classifies which one is intrusion and which one is normal or legitimate. Idss collect network traffic information from some point on the network or computer system and then use this information to.
In this paper we propose a hybrid ids by combining the two approaches in one system. Intrusions detection systems idss are systems that try to detect attacks as they occur or after the attacks took place. Intrusions detection systems idss are systems that try to detect attacks as they occur or after the attacks took place.
Odilia wendel 1 year ago 3 min read. The hybrid ids is. Fundamentally ids recognizes any misuse or unauthorized access which is essentially an attack to the crucial assets of the system or network.
Idss collect network traffic information from some point on the network or computer system and then use this information to secure the network. Misuse detection based idss can only detect known attacks whereas anomaly detection based idss can also detect new attacks by using heuristic methods. Intrusion detection systems can be misuse detection or anomaly detection based.
A hybrid intrusion detection system design for computer network security. A hybrid intrusion detection system design for computer network security journal. A hybrid intrusion detection system design for computer network security.
In different words college. International journal of engineering sciences research technology ijesrt vol7 no. When in comparison with typical paper analysis technique the viewers response system promotes a lot livelier form of teaching.
Intrusion detection concept plays a vital role in personal computer pc security design. Request pdf a hybrid intrusion detection system design for computer network security intrusions detection systems idss are systems that try to detect attacks as they occur or after the.
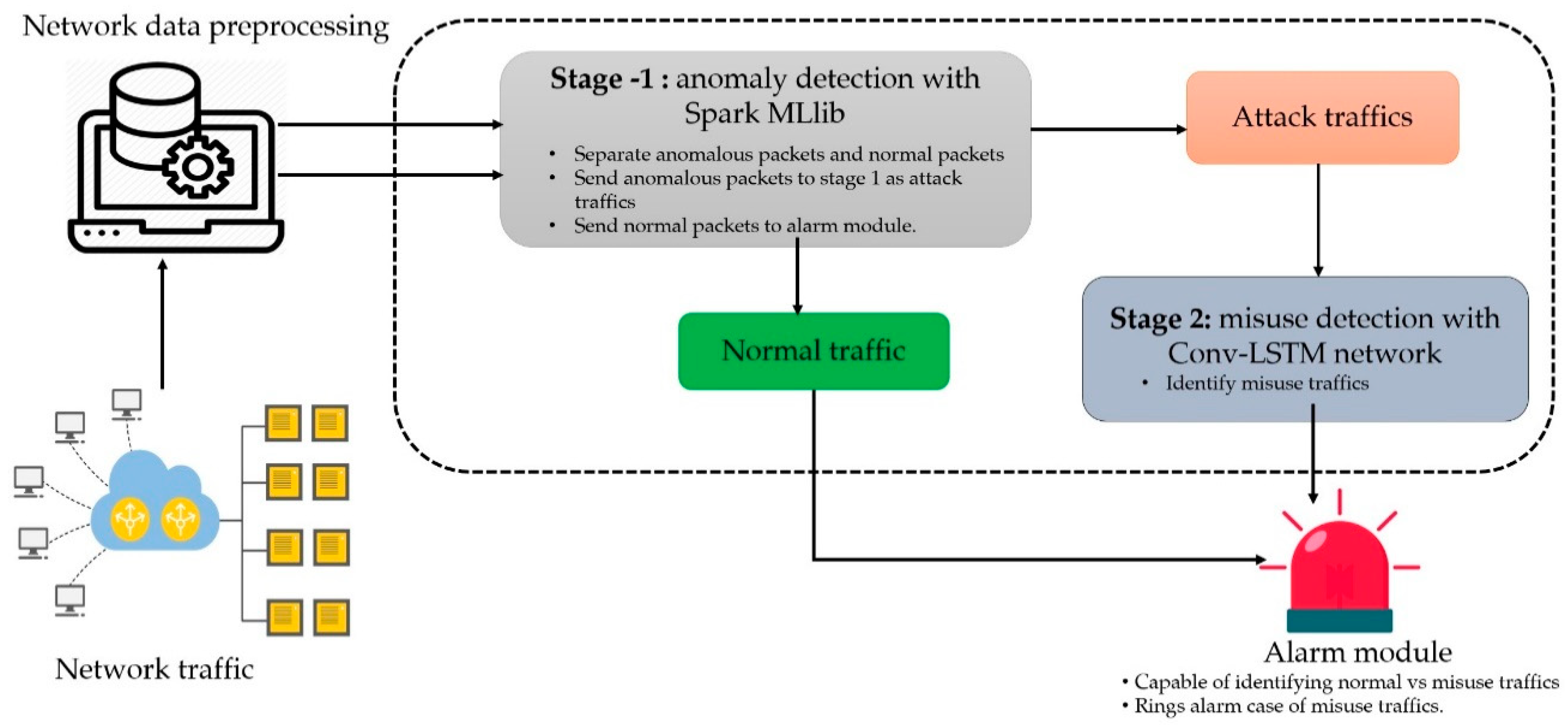 Symmetry Free Full Text A Scalable And Hybrid Intrusion Detection System Based On The Convolutional Lstm Network
Symmetry Free Full Text A Scalable And Hybrid Intrusion Detection System Based On The Convolutional Lstm Network
 Hybrid Intrusion Detection System Technology And Development Semantic Scholar
Hybrid Intrusion Detection System Technology And Development Semantic Scholar
 Hybrid Intrusion Detection System Technology And Development Semantic Scholar
Hybrid Intrusion Detection System Technology And Development Semantic Scholar
 A Hybrid Intrusion Detection System Design For Computer Network Security Sciencedirect
A Hybrid Intrusion Detection System Design For Computer Network Security Sciencedirect
 Hybrid Intrusion Detection System D2h Ids Architecture Download Scientific Diagram
Hybrid Intrusion Detection System D2h Ids Architecture Download Scientific Diagram
 Anomaly Network Based Intrusion Detection System Using A Reliable Hybrid Artificial Bee Colony And Adaboost Algorithms Sciencedirect
Anomaly Network Based Intrusion Detection System Using A Reliable Hybrid Artificial Bee Colony And Adaboost Algorithms Sciencedirect
 Pdf An Architecture Of Hybrid Intrusion Detection System
Pdf An Architecture Of Hybrid Intrusion Detection System

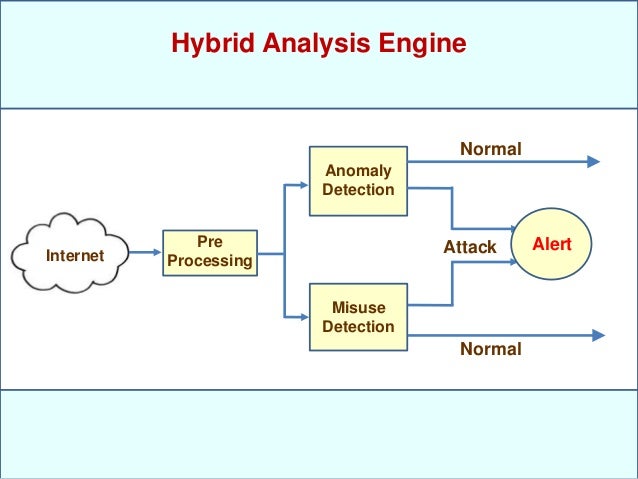 Intrusion Detection With Neural Networks
Intrusion Detection With Neural Networks
 Internal Scheme Of An Intrusion Detection System Download Scientific Diagram
Internal Scheme Of An Intrusion Detection System Download Scientific Diagram
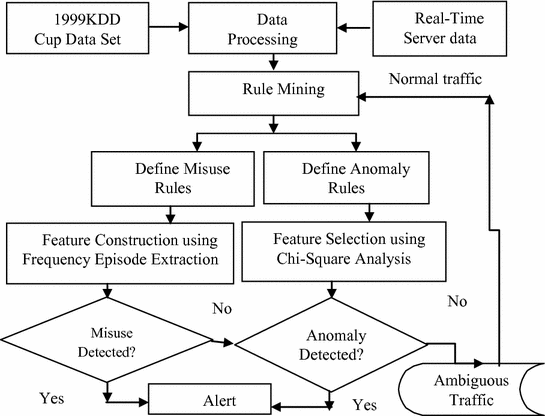 Real Time Hybrid Intrusion Detection System Using Machine Learning Techniques Springerlink
Real Time Hybrid Intrusion Detection System Using Machine Learning Techniques Springerlink