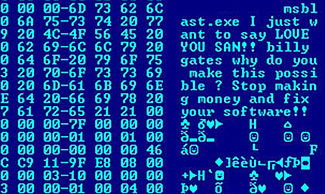
Define The Term Payload As It Pertains To Computer Crime
The destructive event or prank the program is intended to deliver. A payload refers to the component of a computer virus that executes a malicious activity.
 Malicious Payload An Overview Sciencedirect Topics
Malicious Payload An Overview Sciencedirect Topics
define the term payload as it pertains to computer crime
define the term payload as it pertains to computer crime is a summary of the best information with HD images sourced from all the most popular websites in the world. You can access all contents by clicking the download button. If want a higher resolution you can find it on Google Images.
Note: Copyright of all images in define the term payload as it pertains to computer crime content depends on the source site. We hope you do not use it for commercial purposes.
The destructive event or prank the program is intended to deliver.
Define the term payload as it pertains to computer crime. The term botnet means. In some cases this person or group of individuals may be malicious and destroy or otherwise corrupt the computer or data files. Ask question login sign up.
The term payload as it pertains to computer crime is defined as. In addition to the payload such malware also typically has overhead code aimed at simply spreading itself or avoiding detection. Viruses with more powerful payloads tend to be more harmful.
Storing back up files to a server that you get to by going across the internet is. The term payload as it pertains to computer crime is defined as. Computer crime is an act performed by a knowledgeable computer user sometimes referred to as a hacker that illegally browses or steals a companys or individuals private information.
A computer which has been taken over by a hacker which lays dormant until the hacker wakes it up so that the. In computing a payload is the carrying capacity of a packet or other transmission data unit. The term zombie is.
Define the term payload as it pertains to computer crime. Which of the following is a scam in which a perpetrator sends an official looking email that attempts to obtain a users personal and financial information. In computer security the payload is the part of the private user text which could also contain malware such as worms or viruses which performs the malicious action.
Below is a listing of the different types of. Examples of computer crimes. The term payload as it pertains to computer crime is defined as.
The destructive event or prank the program is intended to deliver. The destructive event or prank the virus is intended to deliver a hard disks platters may continue to spin even after power is removed from the computer. The term has its roots in the military and is often associated with the capacity of executable malicious code to do damage.
The term payload as it pertains to computer crime is define as the destructive event or prank the program is intended to deliver the term botnet means a group of compromised computers connected to a network that attacks other networks. Deleting data sending spam or encrypting data. Internet advertising firms often use which of the following to collect information about users web browsing habits.
A group of compromised computers connected to a network that attacks other networks. Which of the following terms is used to describe a program that hides in a computer and allows someone from a remote location to. Apart from the speed in which a virus spreads the threat level of a virus is calculated by the damages it causes.
 Pdf Approach To Solving Cybercrime And Cybersecurity
Pdf Approach To Solving Cybercrime And Cybersecurity
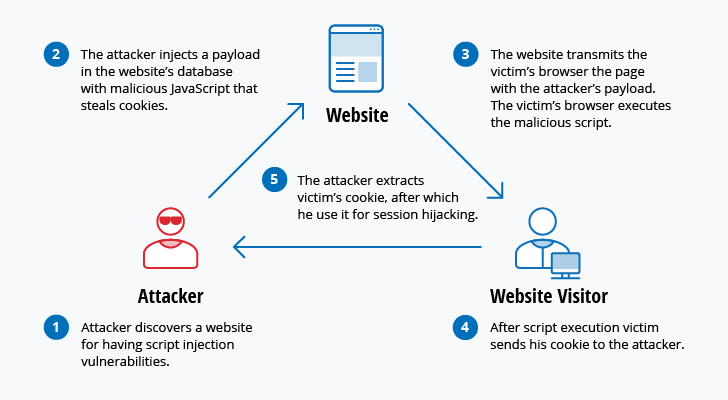 Top 10 Most Common Types Of Cyber Attacks
Top 10 Most Common Types Of Cyber Attacks
The 12 Types Of Cyber Crime Chapter No 2 Fasttrack To Cyber Crime Digit
 The Cyber Security Glossary For Safe Online Experiences
The Cyber Security Glossary For Safe Online Experiences
 Pdf Cyber Security Challenges And The Way Forward
Pdf Cyber Security Challenges And The Way Forward
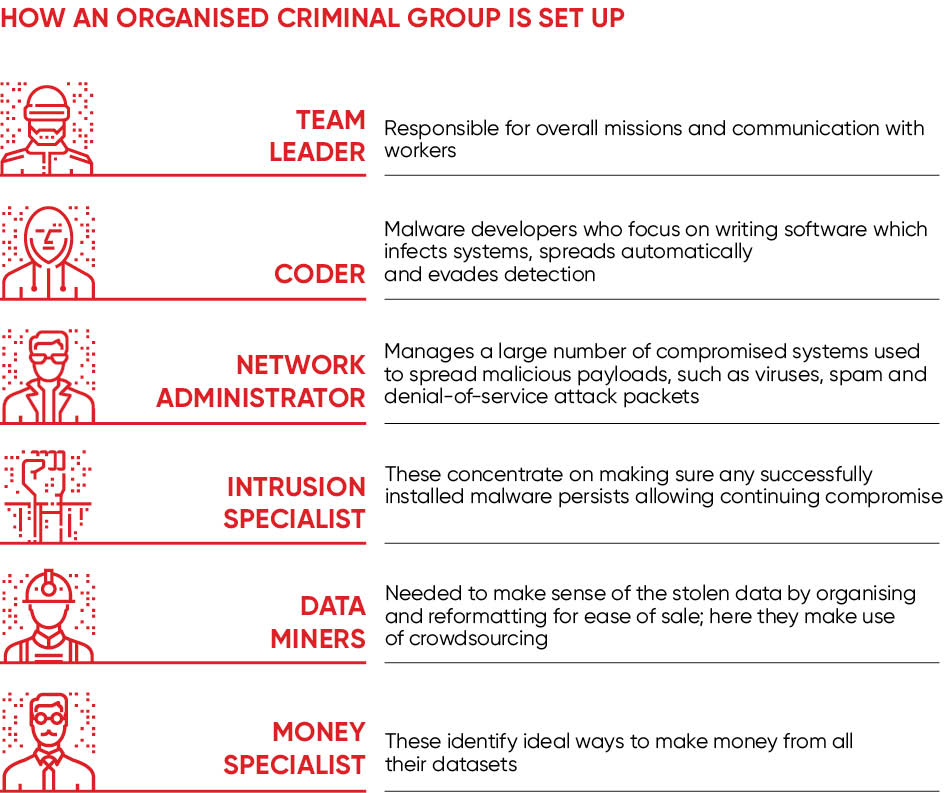 How Organised Is Organised Cybercrime Raconteur
How Organised Is Organised Cybercrime Raconteur
 Cyber Crime Categories And Types The Growth And Progress Of Digital By Ensar Seker Digital Diplomacy Medium
Cyber Crime Categories And Types The Growth And Progress Of Digital By Ensar Seker Digital Diplomacy Medium
The 12 Types Of Cyber Crime Chapter No 2 Fasttrack To Cyber Crime Digit
 Social Engineering Security Wikipedia
Social Engineering Security Wikipedia